
Insider Threat Assessment: Protect Your Business From Within
Are you prepared to tackle the hidden threats within your organization? If left unchecked, insider threats can devastate productivity, morale, and security.

The biggest threat to your organization may already have an all-access pass to your internal workings. Employees or vendors don’t even have to act intentionally to jeopardize your business. Nearly 50% of insider threat incidents result from negligence, such as mistakes, carelessness, or lapses in judgment. However, intentional acts like data theft, fraud, or sabotage can have an even more significant financial impact.
Understanding your organization’s specific insider threats and risks allows you to mitigate them. This post explores how to use an insider threat assessment to help you identify these threats so you can take preventive action.
Download Our Operational Risk Assessment Template
What Is an Insider Threat?
An insider threat is any risk to your organization that arises from an internal party’s access to your systems, assets, or data.
As an example of an insider threat, in 2024, authorities charged a former Google employee with stealing confidential trade secrets tied to the company’s artificial intelligence technology. Prosecutors claim the employee downloaded proprietary files onto personal devices before departing to work for a competitor. These files contained critical details about Google’s AI innovations, potentially jeopardizing billions of dollars in investments. This case is a prime malicious internal threat example, where an individual exploits their authorized access to harm an organization.
In another 2024 incident, Home Depot confirmed a data breach caused by a third-party vendor during system testing. The vendor mishandled sensitive customer information, inadvertently exposing it to unauthorized access by cybercriminals. Unlike the Google case, this breach stemmed from vendor negligence rather than an employee’s deliberate actions, but it still caused damage to the company. In this case, the example of an insider threat is an unintentional one that arose from negligence or a failure to exercise reasonable care when handling company assets, systems, or data.
Despite their differences, both cases qualify as insider threats because they meet a three-tier test:
- The individual or entity had authorized access to company systems, technology, or processes.
- That authorized access was misused, either maliciously or negligently.
- The organization suffered damage, such as operational delays, financial losses, or reputational harm.
Malicious threats vs. unintentional threats
As outlined in the insider threat examples above, actions can be either malicious or unintentional. Malicious cases often result in greater measurable damage, while unintentional incidents can be harder to quantify because the errors are more difficult to identify and trace. While the outcome—harm to your organization—may be similar, the motivations behind these acts are fundamentally different.
| Malicious threats | Unintentional threats |
|
|
Identifying the motivations behind insider threats is crucial for conducting an effective security risk assessment. Understanding behavioral science—whether driven by malicious intent or unintentional mistakes—enables your organization to take targeted actions.
What Is an Insider Threat Assessment?
An insider threat assessment involves identifying, analyzing, and managing the risks your organization faces from employees, vendors, and other authorized system users. In this type of risk assessment, you identify, analyze, and strategize to mitigate or eliminate these potential risks, enhancing your security posture.
This assessment incorporates:
- Identifying risks: Determine specific vulnerabilities posed by authorized users.
- Behavioral analysis: Assess patterns and motivations that may indicate malicious intent or unintentional risks.
- Access review: Evaluate who has access to critical systems and data and whether that access is justified.
- Risk mitigation strategies: Develop plans to address identified risks through monitoring, policies, or controls.
- Continuous monitoring: Establish ongoing processes to detect and respond to emerging threats.
Using a risk matrix as an insider risk assessment tool, you can prioritize insider threats based on their likelihood and impact, ensuring that the most critical threats are addressed first. This approach allows you to categorize insider threats into different levels of severity, from low to high, helping you focus resources on the most dangerous threats—such as malicious data theft or sabotage—that could cause the most harm to your organization.
Here is an example of what a risk matrix might look like for some business risks familiar across industries:
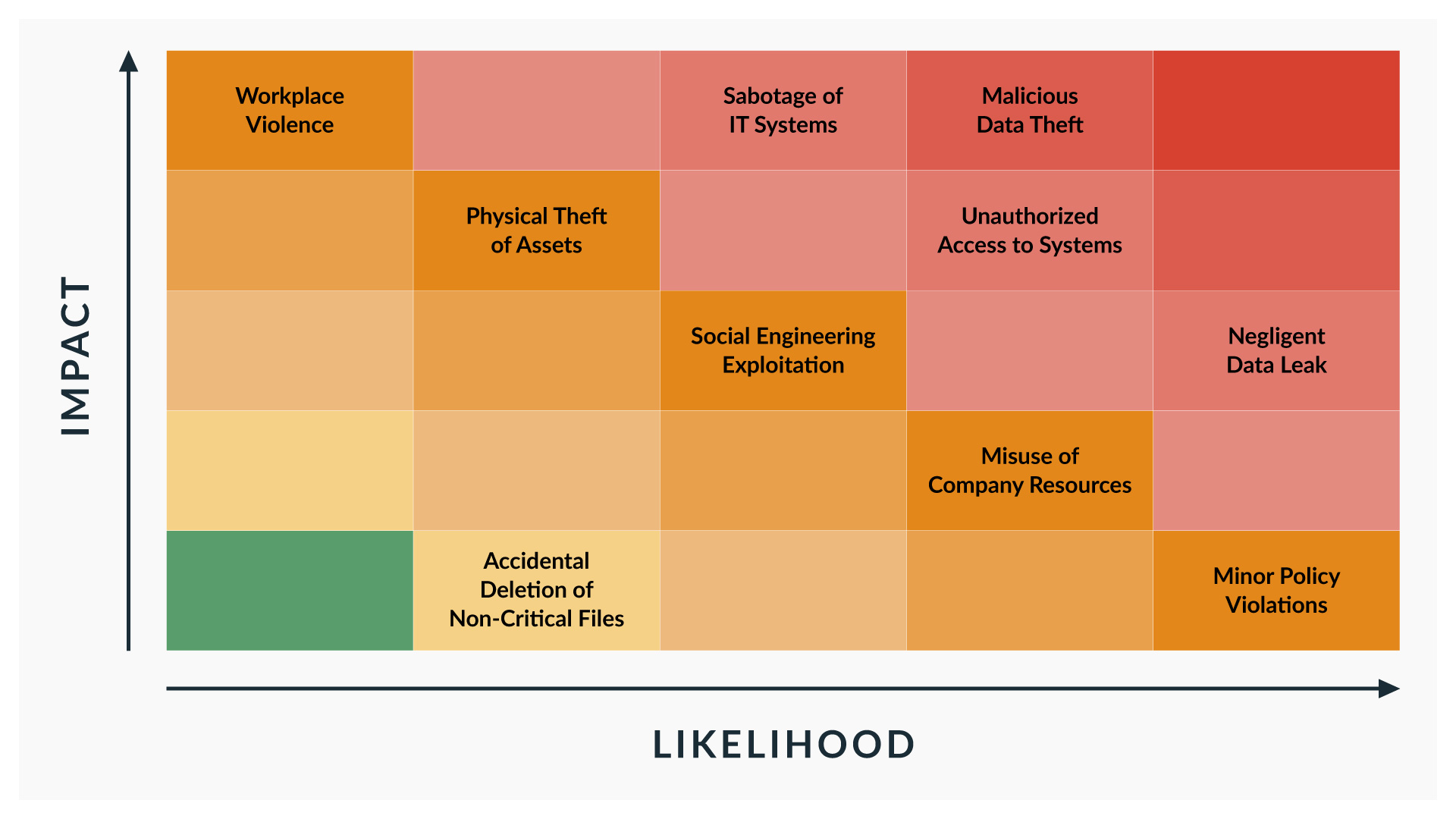
The Importance of Assessing Insider Threats and Their Impacts
Most business leaders understand the importance of comprehensive risk management programs, which often include insider risk assessments as a small but crucial component. These threats are particularly pervasive, and their consequences can ripple beyond the immediate impact. Here’s a closer look at the risks insider threats pose:
Effects on workforce productivity and morale
Tensions in the workplace inevitably impact employee well-being and productivity. Whether intentional or inadvertent, insider threats amplify these issues by fostering distrust, uncertainty, and stress among employees. These conditions can lead to lower engagement, increased absenteeism, and decreased productivity.
Workplace violence represents one of the most severe examples of physical security threats and their impact on productivity and morale. As Director of Corporate Safety and Security at TaylorMade Golf, Louis Duran highlighted during a recent interview on The Employee Safety Podcast that workplace violence often arises from internal sources—such as disgruntled employees or unresolved interpersonal conflicts—rather than external threats.
Duran draws an analogy to asymmetrical threats, explaining that while we once focused on external “symmetrical” threats, like an outsider attempting to harm the organization, today, the real risk often comes from individuals within the company. These incidents disrupt day-to-day operations and create a lasting sense of fear and insecurity among staff.
— Louis Duran, Director of Corporate Safety and Security at TaylorMade Golf
Duran recalls an incident at TaylorMade where an employee quit abruptly and displayed aggressive behavior by throwing objects at a supervisor. While the situation was resolved without harm, it required the implementation of de-escalation strategies and pre-emptive communication plans to ensure the safety of others in the workplace.
These types of incidents have a profound impact on morale. When employees witness or hear about violence in the workplace, it can create a sense of fear and uncertainty. Even if an incident is resolved without physical harm, the psychological effects can linger, leading to disengagement and reduced productivity.
Fines, penalties, and compliance violations
A simple unintentional act by an employee or vendor can result in significant fines and penalties, especially for companies in highly regulated industries.
For example, in October 2022, Interserve Group Limited, a U.K.-based company, experienced a significant data breach after an employee clicked on a phishing email. This unintentional action allowed attackers to install malware, compromising sensitive data belonging to up to 113,000 current and former employees. The breach exposed critical gaps in compliance with the U.K. GDPR. Ultimately, the Information Commissioner’s Office fined Interserve £4.4 million for their failure to protect employee data and implement appropriate safeguards.
The risk of fines, penalties, and other violations exceeds the immediate impact. The problem may surface for years in system audits or evaluations, creating a lasting black mark for the company that takes years to overcome.
Reputational damage
Insider threats are particularly dangerous for an organization’s reputation because employees are often seen as extensions of the organization. When using the organization’s official channels, employees can do serious and long-term damage to a brand’s reputation.
For example, in 2013, HMV, a British entertainment retail company, faced a public relations crisis when laid-off employees took over the company’s official social media account. Disgruntled workers live-tweeted details of the firing process, openly criticizing management and sharing internal decisions. The incident quickly gained media attention, damaging the company’s image during an already difficult time.
In an era where layoffs and restructuring are more common due to economic uncertainty, organizations must implement robust measures to ensure only authorized personnel can post on official accounts. Equally important, however, is creating clear, compassionate communication strategies to address employees’ concerns during sensitive transitions. Transparency, empathy, and proactive engagement with staff can help reduce the likelihood of mass discontent spilling onto public platforms.
Loss of intellectual property or trade secrets
In some cases, an insider threat could stem from your competitors. There are many examples of individuals joining innovative companies with the express intention of stealing trade secrets.
For example, Tesla filed a lawsuit against Rivian Automotive in July 2020, alleging that Rivian poached Tesla employees and encouraged them to steal confidential engineering and battery technology information. The lawsuit claimed Rivian systematically recruited former Tesla employees, leveraging their access to proprietary data. The case escalated when, in July 2024, a California judge ruled that Rivian would face trial for these allegations.
Aside from the potential costs of the legal battle, if the allegations are true, Tesla lost critical trade secrets that it can never recover due to this insider threat, potentially harming its competitive advantage.
Long-term financial impacts of insider attacks
Fines and penalties are only one side of the coin regarding the financial impacts of insider threats. Your organization’s exposure to liability can far exceed those initial costs through lawsuits and loss of customer goodwill.
One example comes from Morgan Stanley’s 2016 data loss incident. The company discovered that a third-party vendor responsible for decommissioning its data centers had failed to wipe customer data from servers before selling them. This insider threat—a lapse by an authorized vendor—resulted in a significant breach of customer trust and legal exposure.
While Morgan Stanley faced a $60 million fine from the Office of the Comptroller of the Currency, the financial fallout didn’t end there. In January 2022, six years after the original incident, Morgan Stanley agreed to pay an additional $60 million to settle a class-action lawsuit filed by affected customers. The settlement illustrates how insider threats can impose long-term financial burdens, with organizations continuing to pay for lapses years after the event.
Conducting insider threat assessments is critical to enhancing your organization’s ability to effectively address changing and growing risks. As threats continue to evolve, failing to perform regular and thorough assessments leaves your organization vulnerable to a host of issues. Risk assessments provide the insight needed in risk identification and control measures.
How to Conduct an Insider Threat Assessment
While the response to every insider threat will differ, the evaluation process will remain largely the same. There are five broad steps: identifying insiders and access rights, establishing risk behaviors to monitor, analyzing whether the behaviors make sense in context, mitigating or eliminating the threat, and using past incidents to shape future policies.
1. Identify insiders and their access rights
Defining “insiders” may seem straightforward—typically, they’re your employees. However, insiders can also include contractors, vendors, and third-party organizations with access to your systems or sensitive information.
Conducting an insider inventory is essential. This process identifies all individuals—employees and non-employees—who interact with your internal systems. Using a qualitative risk analysis, you can assess the potential impact of these insiders on your organization, prioritizing higher-risk individuals and creating tailored mitigation strategies.
Here are some examples of non-employee workers who may have insider access that requires careful monitoring and management:
|
|
|
|
2: Establish insider threat risks to monitor
Risk behaviors will vary depending on an individual’s role and whether you are monitoring for malicious or negligent actions. Malicious acts are often easier to identify, while negligent behaviors—such as sharing passwords or failing to follow privacy policies—can be more challenging to identify. Here are some behavioral indicators to look for during an assessment:
| Malicious threat behaviors | Negligent threat behaviors |
|
|
3: Analyze context in user activity
It’s not enough to simply monitor for behaviors that could indicate an insider threat; you must also review them in context. Otherwise, you risk spending most of your time categorizing false positives rather than focusing on the real threats that pose an actual risk. Let’s examine a scenario to illustrate how this happens.
At a major technology company, a newly hired employee begins to exhibit concerning behavior by showing an obsessive interest in a project they aren’t assigned to. They consistently approach team members for detailed information, pushing for access to confidential files and systems despite lacking the necessary permissions.
Without context, this could easily be flagged as a malicious insider threat. However, the situation becomes clearer when viewed in light of the rest of the company’s data. The employee’s human resources file shows they are enrolled in a certification program directly related to that technology. The hiring management platform reveals that they originally applied for a role on that team but were deemed not to have the appropriate experience. Background checks show no prior unethical actions or connections with competitors and no major financial issues.
This additional context suggests that the employee is likely just an enthusiastic newcomer eager to learn and get involved with a project that aligns with their interests. They may need a refresher on the appropriate use of company resources, but there’s little reason to suspect any malicious intent.
With context, your incident response changes. You can focus on the actual risks while avoiding unnecessary alarm over relatively benign behaviors.
4: Mitigate or eliminate potential insider threats
Insider threat management is a broad topic that could fill an entire blog post. To briefly cover it here, there are generally two responses: mitigate or eliminate the threat. The appropriate response often depends on whether the threat is malicious or negligent.
The typical approach to malicious threats is to eliminate them immediately. Time is critical, and correcting the behavior may not be possible. For example, an employee caught stealing insider information would be terminated immediately, or a vendor who shared data with an unauthorized third party for personal gain would have their contract terminated and voided.
For unintentional insider threats, the approach is typically mitigation through training, policy, and access controls. Remedial training can help guide employees or vendors toward the correct actions. New policies and procedures are communicated clearly to ensure proper actions are taken. The goal is to educate and improve behavior to prevent future incidents rather than immediately severing ties.
In both cases, the key is to assess the situation and choose the best course of action to protect the organization while ensuring fairness. Your response can guide future policy development and improvement.
5: Use the past to define the future insider threat program
Every insider threat your organization faces is an opportunity to learn. After discovering and managing an insider threat, it’s essential to conduct an after-action review (AAR) and complete a report. The AAR covers four sections:
- Post-incident recap: Who was involved, and how were you supposed to respond?
- Outcome review: What actually happened?
- Incident analysis: What went well and why?
- Potential improvements: What can be improved and why?
For example, consider a situation where an employee is caught stealing trade secrets for a competitor, though the company was able to intervene. Here’s what a brief AAR might look like:
Post-incident recap
Employee X, a senior product manager, was suspected of leaking sensitive data to a competitor. The initial response was to suspend their permissions to internal systems and initiate an investigation.
Outcome review
The employee was caught attempting to email proprietary information to an external account. The company’s user activity monitoring system flagged the action, and the employee was confronted before the data was transmitted.
Incident analysis
The company’s monitoring system worked as intended, and the intervention happened swiftly, preventing further damage. Communication between the IT and HR departments was clear, and the investigation was thorough.
Potential improvements
One key oversight was in the hiring process. The employee’s history of questionable behavior wasn’t properly vetted during onboarding. This incident highlighted the need for a more thorough background check and screening process for individuals in sensitive roles.
With the completed analysis, the company can now use the information learned to adapt its policy on insider threat detection. For example, it may require those in project manager roles to undergo more thorough background checks, specifically looking for signs of previous unethical behavior, financial instability, or any history of actions that could pose a risk to the organization.
In addition to adjusting policies, the company can use tabletop exercises to test out different insider threat scenarios in a controlled setting. These exercises simulate real-world situations, allowing the company to assess how the new policies and processes would work in practice, identify potential weaknesses in their response plans, and refine their approach.
Improving Insider Threat Mitigation and Risk Management
Your insider threat assessment is only a small part of your operational risk assessment, but it shouldn’t be overlooked. Your employees are both your biggest asset and your most significant liability. That’s why your insider threat assessment process must be continuous. The historical data in your information systems will guide your response and help you adapt to new and unprecedented challenges.
However, insider threats are just one piece of the puzzle. To better understand your organization’s overall risk exposure, assess other potential vulnerabilities as well. Converged security, which integrates physical security, cybersecurity, and personnel security, offers a more holistic view of risk, ensuring you can address threats from multiple angles. This integrated approach strengthens your ability to identify and mitigate risks, both from insiders and external sources, in a more coordinated and effective way.
We encourage you to download our Occupational Risk Assessment Template, which provides a comprehensive framework to identify and address various risks within your organization.




