
Qualitative Risk Analysis & Other Types of Risk Assessment
Choosing the right risk assessment methodology, whether qualitative, quantitative, or both, is crucial for effectively managing threats.

“Research the threat and apply data from sources like public records, social media, dark net—so that you can learn as much as possible.”Lukas Quanstrom Co-Founder and CEO, Ontic
When is a threatening letter to a business more than an empty threat? How do you determine when it becomes a genuine risk? Lukas Quanstrom, co-founder and CEO at Ontic, regularly confronts these challenges. In a recent interview on The Employee Safety Podcast, Quanstrom shared how understanding the severity of such threats requires more than surface-level analysis. It requires a detailed, strategic, and proactive approach.
“Once a potential threat has been identified, the next step is to research the threat and apply data from sources like public records, social media, dark net—so that you can learn as much as possible,” Quanstrom said. Research and assessment are critical to understanding how to manage business threats, and there are a few different risk assessment methodologies, each with its strengths and formats.
These strategies range from a qualitative risk analysis that relies on expert judgment and scenario analysis to quantitative methods that use statistical data and mathematical models. Some methodologies even sit squarely in the middle, using descriptions and data to establish a risk management program. Picking the correct method will help you manage threats against your business by providing a structure to understand the likelihood and impact of those threats.
Download Our Operational Risk Assessment Template
Risk Identification and Risk Responses
When assessing risks, it’s essential to recognize that various types of risks can affect a business. This article will focus on four key categories of risk: strategic, compliance, financial, and operational risk. But it’s important to remember that these are just a few examples of the broad range of risks businesses may encounter.
| Strategic risk | Compliance risk | Financial risk | Operational risk |
| Risks arising from adverse business decisions, poor implementation, or a lack of responsiveness to industry changes. (e.g., a new competitor enters the market) | Risks related to legal requirements, regulations, or internal policies—which can lead to legal penalties, financial forfeiture, and reputational damage. (e.g., a new privacy law is introduced) | Risks involving potential financial losses due to market fluctuations, credit risk, liquidity issues, and investments. (e.g., interest rates rise on a business loan) | Risks from failures in processes, people, systems, or infrastructure. (e.g., a cybersecurity incident takes out company networks and infrastructure) |
A practical risk assessment aims to better understand how to manage those risks. These are the four primary risk management responses:
- Avoidance: Eliminating the risk
- Mitigation: Reducing the impact or likelihood of the risk event
- Transfer: Shifting the risk to another party, such as through insurance
- Acceptance: Acknowledging the risk and choosing to deal with its potential consequences
Your chosen risk assessment methodologies will help you understand the threats your business faces and choose from one of the above options for handling them. With thorough analysis, you can make informed decisions that align with your organization’s risk tolerance and strategic goals.
3 Risk Assessment Methodologies
The steps of a risk assessment are relatively straightforward: identify threats, assess those threats, develop controls, and evaluate your response.
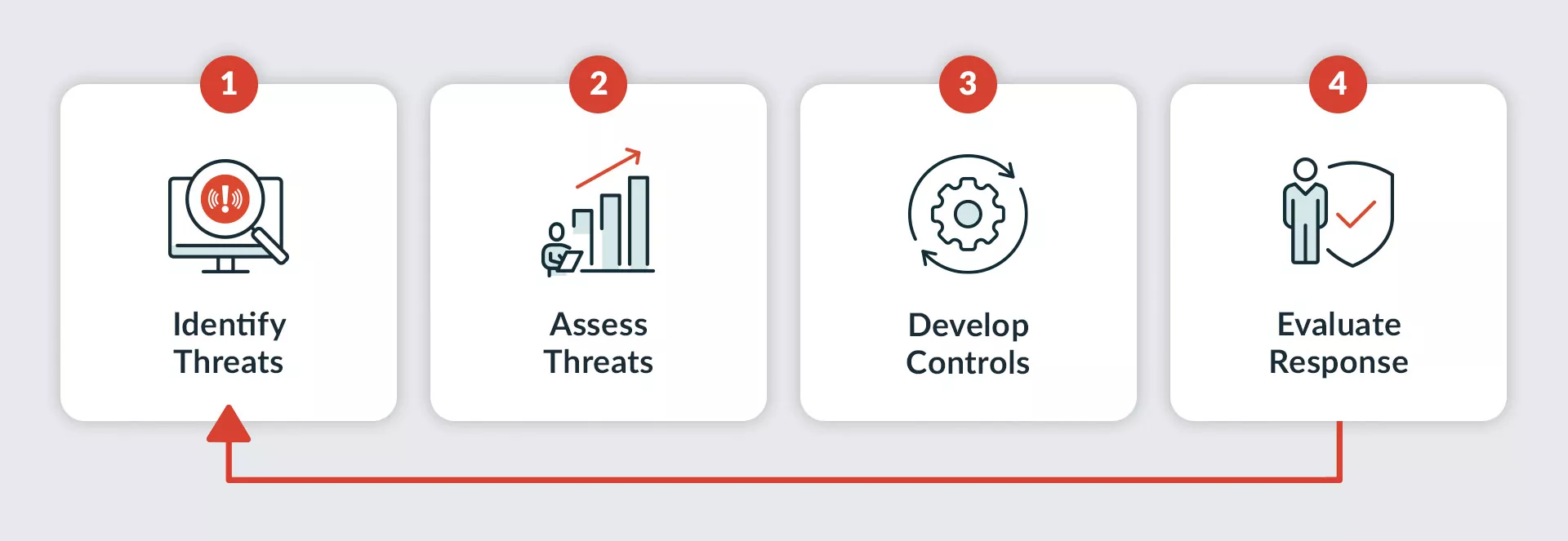
However, these four steps leave much room for interpretation—and error. A risk assessment methodology is a systematic approach underlying all four stages by qualifying or quantifying the threat. That is why most risk assessments use one of these three methodologies:
- Qualitative: Determining risks based on subjective judgment and descriptive measures rather than numerical data or statistics.
- Quantitative: Evaluating risks by estimating specific threats’ probability and potential impact using numerical data and statistical methods.
- Semi-Qualitative: Combining aspects of both qualitative and quantitative analysis.
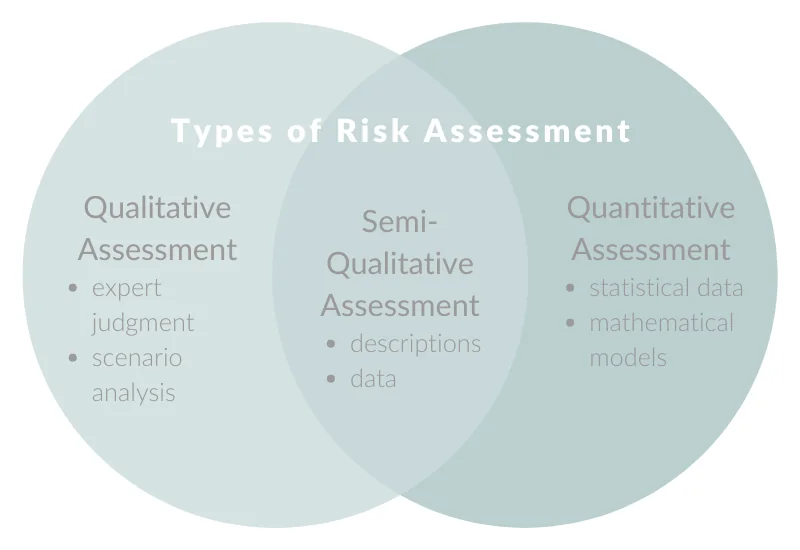
Qualitative vs. quantitative risk analysis, with a blended assessment option
Qualitative Risk Analysis
Qualitative risk assessments are a type of risk evaluation that relies on subjective judgment and expert opinions rather than numerical data. This methodology is beneficial when data is unavailable, incomplete, or difficult to quantify. Qualitative risk assessments often involve identifying potential risks through brainstorming sessions, expert interviews, and workshops. These assessments rely on scenarios and descriptive analysis to evaluate the likelihood of occurrence and impact of risks.
One key benefit of qualitative risk assessments is their flexibility. They can be tailored to fit a business’s needs and context, making them highly adaptable to various industries and situations. Unlike quantitative assessment methods, which require detailed data and statistical models, you can perform a qualitative risk analysis with limited information and still consider a broad range of risks.
Another benefit is their ability to incorporate the insights and expertise of individuals who may deeply understand potential risks but lack access to comprehensive data. This subjective approach can provide valuable context and nuance that quantitative methods might overlook.
Numerous customized qualitative risk assessment models are available, with several well-established methodologies, such as those from the International Organization for Standardization (ISO), gaining widespread recognition for their effectiveness. These methodologies offer structured approaches to identifying and analyzing risks based on expert judgment and descriptive analysis.
ISO 27001
ISO 27001 is a qualitative strategy typically associated with cybersecurity, but its influence can extend into other domains. It is tailored to establish, implement, maintain, and continuously improve information security management systems (ISMS) to safeguard sensitive information.
This widely recognized qualitative risk assessment methodology is primarily associated with cybersecurity, though you can apply its principles across various domains. This standard provides a structured approach for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS) to protect sensitive information.
An ISO 27001 assessment focuses on three critical areas—people, processes, and technology.
- People: This involves assessing risks related to employees and other individuals with sensitive information access. It includes evaluating the effectiveness of training programs, identifying potential insider threats, and ensuring that roles and responsibilities for information security are clearly defined and communicated.
- Processes: This area focuses on evaluating and improving the procedures and policies to manage information security. It includes reviewing existing security policies, conducting risk assessments, and implementing controls to address identified risks. Regular audits and reviews are part of this process to ensure that procedures remain effective and are updated as needed.
- Technology: This involves assessing the technical controls and systems that protect sensitive data. It includes evaluating the security of IT infrastructure, software, and hardware and then implementing measures such as encryption, access controls, and monitoring systems to prevent and respond to security incidents.
By addressing these three critical areas, ISO 27001 helps organizations systematically identify, mitigate, and manage risks to information security.
Decision trees
A decision tree is a dynamic risk assessment tool that uses a diagrammatic approach to map out possible outcomes and their associated risks for decision-making. Seeing a visual representation of the flow can often help stakeholders understand the potential consequences of each decision branch.
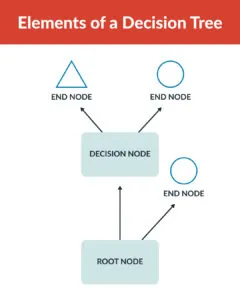 This method clarifies the sequence of events and allows for evaluating probabilities at each decision point, enabling more informed and structured choices. Decision trees are particularly useful in complex scenarios where multiple variables and uncertainties need to be considered, providing a systematic framework for evaluating options and their implications.
This method clarifies the sequence of events and allows for evaluating probabilities at each decision point, enabling more informed and structured choices. Decision trees are particularly useful in complex scenarios where multiple variables and uncertainties need to be considered, providing a systematic framework for evaluating options and their implications.
As the diagram above shows, decision trees have three components: the root, the decisions, and the endpoints.
- Root: The root of a decision tree represents the starting point or initial decision that needs to be made.
- Decisions: Decision nodes are points within the decision tree where choices or alternatives are considered. Each decision node branches out into one or more possible outcomes or actions that can be taken based on the decision made at that point.
- Endpoints: These are the outcomes or results of following a specific path through the decision tree. They represent the consequences or outcomes of the decisions made at each preceding node.
You can apply many qualitative methodologies to improve risk assessments, but they’re not always ideal because they lack precision and quantifiable metrics. While qualitative approaches provide valuable insights into subjective factors such as organizational culture and human behavior, they may struggle to deliver measurable and comparable data points for rigorous analysis and decision-making. This is where semi-qualitative risk assessment methodologies become invaluable.
Quantitative Risk Evaluation
Quantitative risk assessments involve assigning numerical values to potential threats, allowing organizations to evaluate the likelihood of risks, predict their impacts, and estimate potential losses. This data-driven approach provides a precise measurement of risk, which can be invaluable for businesses looking to make informed decisions based on empirical evidence.
A business chooses this risk assessment approach for a few different reasons. Some of the significant benefits of a quantitative risk assessment are:
- Increased accuracy: Quantitative risk assessments provide precise numerical data, which helps businesses measure risk more accurately than qualitative methods that rely on subjective judgment.
- Enhanced objectivity: Quantitative assessments minimize personal biases with statistical data and mathematical models, offering a more objective risk evaluation than qualitative approaches.
- Improved comparability: Quantitative data allows for direct comparison between different risks, which is often more challenging with qualitative assessments that may use descriptive or subjective criteria.
- Better forecasting: Quantitative methods use historical data to predict future risk scenarios, offering more reliable forecasting capabilities than qualitative methods that may not use historical data as effectively.
- Clear communication: Quantitative results provide concrete numbers that can be easier to communicate and justify to stakeholders, as opposed to qualitative descriptions that might be more open to interpretation.
- Benchmarking and performance measurement: Quantitative data enables benchmarking against industry standards and measuring performance over time, which qualitative methods may not directly support.
One standard quantitative risk methodology involves using historical weather data and statistical models to predict the probability of a hurricane occurring in a specific area. Meteorologists might analyze past hurricane patterns, sea surface temperatures, and atmospheric conditions to calculate the likelihood of a hurricane’s landfall in a given region over the next year. They pass this information on to businesses that use quantitative data to manage the risk.
Businesses in vulnerable areas can prioritize risks and management efforts by assigning numerical probabilities to different levels of hurricane risk. For example, a company operating in a region with a high probability of hurricanes might invest in enhanced building infrastructure and emergency response plans. At the same time, a business in a lower-risk area might allocate fewer resources to hurricane preparedness. This data-driven approach allows for targeted risk mitigation strategies based on quantified risk probabilities.
Another example of quantitative risk assessment involves using financial models to predict the effects of changes in interest rates on a company’s bottom line. A company with significant debt might use historical interest rate data and financial modeling techniques to estimate how fluctuations in interest rates could impact its interest expenses and overall profitability.
The company can project potential financial outcomes under different interest rate scenarios by applying quantitative methods, such as sensitivity analysis or scenario modeling. For example, if interest rates are predicted to rise by 1%, the company can estimate the increase in interest payments and its effect on net income. These insights allow the business to make informed decisions about financial strategies, such as refinancing debt or adjusting investment plans, based on numerical projections of potential impacts.
How to Conduct a Risk Assessment
This video will help you facilitate an effective risk assessment at your organization.
Semi-Qualitative Risk Assessment Tools
Semi-qualitative risk assessment methodologies combine the precision of quantitative data with the depth of qualitative analysis, offering a thorough and rigorous approach to understanding risks. This method leverages numerical data to provide concrete risk probability and impact estimates while incorporating qualitative insights to capture nuances that numbers alone may not reveal.
Semi-qualitative assessments enable organizations to examine risks from multiple angles by integrating data-driven and judgment-based perspectives. This comprehensive approach ensures that potential threats are evaluated in terms of statistical likelihood while considering contextual implications and expert opinions.
This combined approach results in a more complete risk profile, facilitating better-informed decision-making. Organizations benefit from a detailed understanding of risks, allowing them to develop strategies that address both the measurable and less quantifiable aspects of potential threats.
Risk matrix
A risk matrix is the most straightforward semi-qualitative approach. This tool categorizes direct risks based on their likelihood and potential impact, as depicted below.
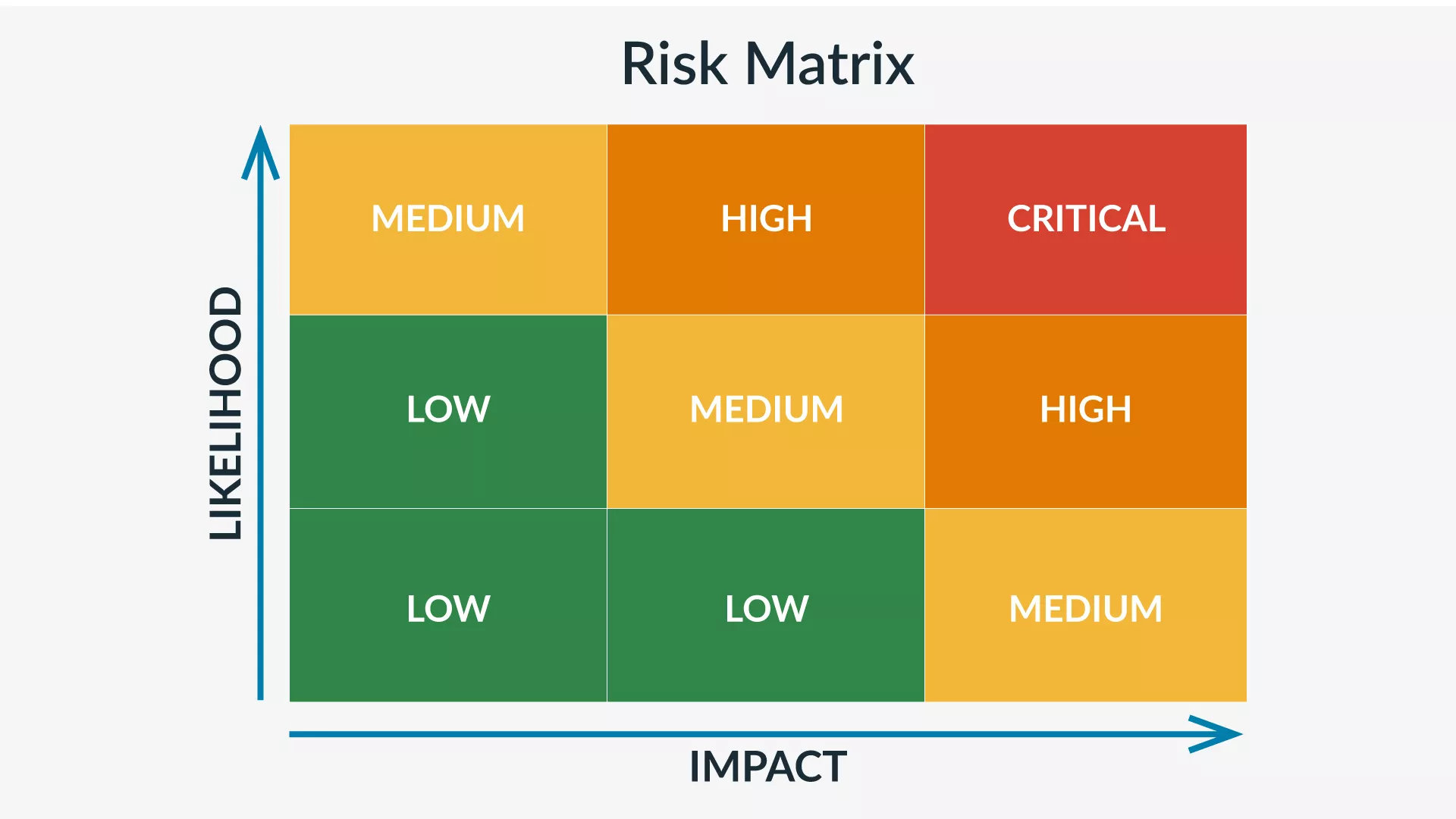
Using a risk matrix enables efficient risk management through hazard identification and categorization. The tool weighs risks based on their likelihood and impact, visually presenting the severity of each risk scenario. Using a risk matrix—especially along with a risk register—organizations can prioritize resources and efforts toward mitigating significant, high risks while effectively communicating the rationale behind risk management decisions to key stakeholders.
Suppose the risk matrix is a straightforward example of a semi-qualitative methodology. In that case, an integrated threat intelligence system represents the opposite end of the spectrum with more detailed analysis.
Integrated threat intelligence system
Threat intelligence systems gather and analyze comprehensive information about potential hazards, aiding organizations in proactive risk mitigation and response strategies. They can also be critical tools for assessing and understanding your specific risks. In his interview, Lukas Quanstrom also highlighted the evolving role of threat intelligence in proactive corporate security risk assessment. Quanstrom emphasized that traditional reactive threat management is giving way to a more proactive approach enabled by what he terms “protective intelligence.”
Protective intelligence integrates investigative (qualitative) techniques with advanced analytics (quantitative) to detect and assess potential threats early on. These indicators, such as threatening communications or unusual patterns in employee behaviors, serve as early warning signals that enable proactive risk mitigation strategies. Using data to define a threat’s likelihood and impact allows organizations to prioritize strategies.
Quanstrom explained, “By adopting a proactive, always-on security approach, you can continually collect and connect pre-incident physical threat indicators, providing the critical knowledge needed to prevent bad things from happening.” This proactive stance safeguards assets and personnel, supports business continuity, and enhances stakeholder confidence in the organization’s resilience to emerging threats.
Combining Risk Analysis Processes
Qualitative, quantitative, and semi-qualitative risk assessment methodologies have strengths and limitations. Integrating all three of these approaches offers you a more comprehensive risk assessment so you better understand your potential threats and vulnerabilities. With that situational awareness, you can make informed decisions and prioritize resources where they are most needed.
By combining qualitative insights with quantitative data and semi-qualitative assessments, businesses can establish a dynamic risk management plan that adapts to identified risks and enhances overall resilience.






