
How to Perform a Security Risk Assessment in 5 Steps
Protecting your organization starts with a thorough security risk assessment. In this post, we’ll explore how to identify threats, assess risks, and apply practical tools to safeguard your operations.

What keeps you up at night? For safety professionals, it’s the constant worry of risks going unnoticed—whether it’s an accident waiting to happen, a hidden danger, or a data breach. Every organization faces security and safety challenges, but you can’t address threats you’re unaware of.
A security risk assessment—or an SRA—helps you identify potential risks, from unsafe conditions to physical break-ins, and gives you the knowledge to protect your assets, employees, and reputation. In this post, we’ll break down the risk assessment process, why it matters, and simple steps to get started—so you can stay ahead of whatever’s lurking.
Download Our Threat Assessment Template
What Is a Security Risk Assessment?
A security risk assessment (also called a threat assessment) identifies, evaluates, and ranks potential problems that could harm an organization’s people, assets, or operations. This structured methodology reveals security gaps or weaknesses, so you can address them proactively before real threats arise.
A security risk assessment covers a wide range of situations, including:
- External hazards originating from outside the organization
- Internal or “insider” threats, posed by employees or individuals with internal access
- Physical security threats involving unauthorized access to buildings, server rooms, and other sensitive areas
- IT security threats including cyberattacks, unauthorized access to systems, data breaches, and service disruptions
We’ll outline a full list of potential threats to consider a bit later. For now, just know that risks may be internal or external, physical or digital, and human-based or environmental. Basically, anything that has the potential to harm your people, assets, or business operations would be covered by a security risk assessment.
The process typically involves reviewing and testing systems, people, and processes, ranging from HR policies and physical security controls to firewall configurations. You’ll document the results in a report, along with specific plans for improvement.
Security risk assessment vs physical security assessment
While these terms are often used interchangeably, they address distinct aspects of security. You can prevent gaps in your defenses by knowing how they complement each other.
A physical security assessment focuses on tangible vulnerabilities within facilities and infrastructure. A security risk assessment is more holistic—it evaluates your organization’s overall security posture, covering digital, physical, and operational risks.
Together, these reviews support a converged security approach, integrating physical and cybersecurity measures for a comprehensive defense against potential threats.
Does your business need a security risk assessment?
The biggest question for busy safety leaders is often “Is a security risk assessment worth my time and effort?” In short, yes.
According to the Allianz Risk Barometer, cyber incidents, business interruption, and natural catastrophes are the top risks for businesses in 2024. At the same time, a majority of executives sense that the volume and complexity of risks are increasing. Between evolving regulations, rising geopolitical tensions, a hybrid workforce, and the emergence of AI, it’s not hard to see where these sentiments stem from.
By conducting a risk assessment, your organization can develop risk mitigation strategies to protect employees, facilities, and operations from disruptive or potentially catastrophic events.
Being prepared and informed helps you respond faster, work more effectively, and reduce damage. But that’s just the start:
- Many industries require security risk assessments to meet compliance standards like HIPAA, PCI-DSS, SOX, and GDPR—and staying compliant avoids expensive fines.
- Prioritizing risks ensures your security budget targets the most critical areas that need protection.
- Security risk assessments provide insights that improve decisions about security, infrastructure, and staffing.
- Regular assessments show your commitment to security, which builds trust and loyalty with customers and employees.
- With cyber threats on the rise, IT experts recommend conducting at least one risk assessment yearly as part of your cybersecurity plan.
- Some insurance companies may require an assessment before granting approval.
Security Risk Assessment Templates & Tools
The good news is that a risk assessment doesn’t have to be difficult, time-consuming, or costly. There are a number of tools out there to help you get it done quickly and efficiently.
Risk matrix
A risk matrix (also known as a probability or impact matrix) is a simple, free tool that helps you visualize the likelihood and impact—essentially, the amount of damage—of a potential threat.
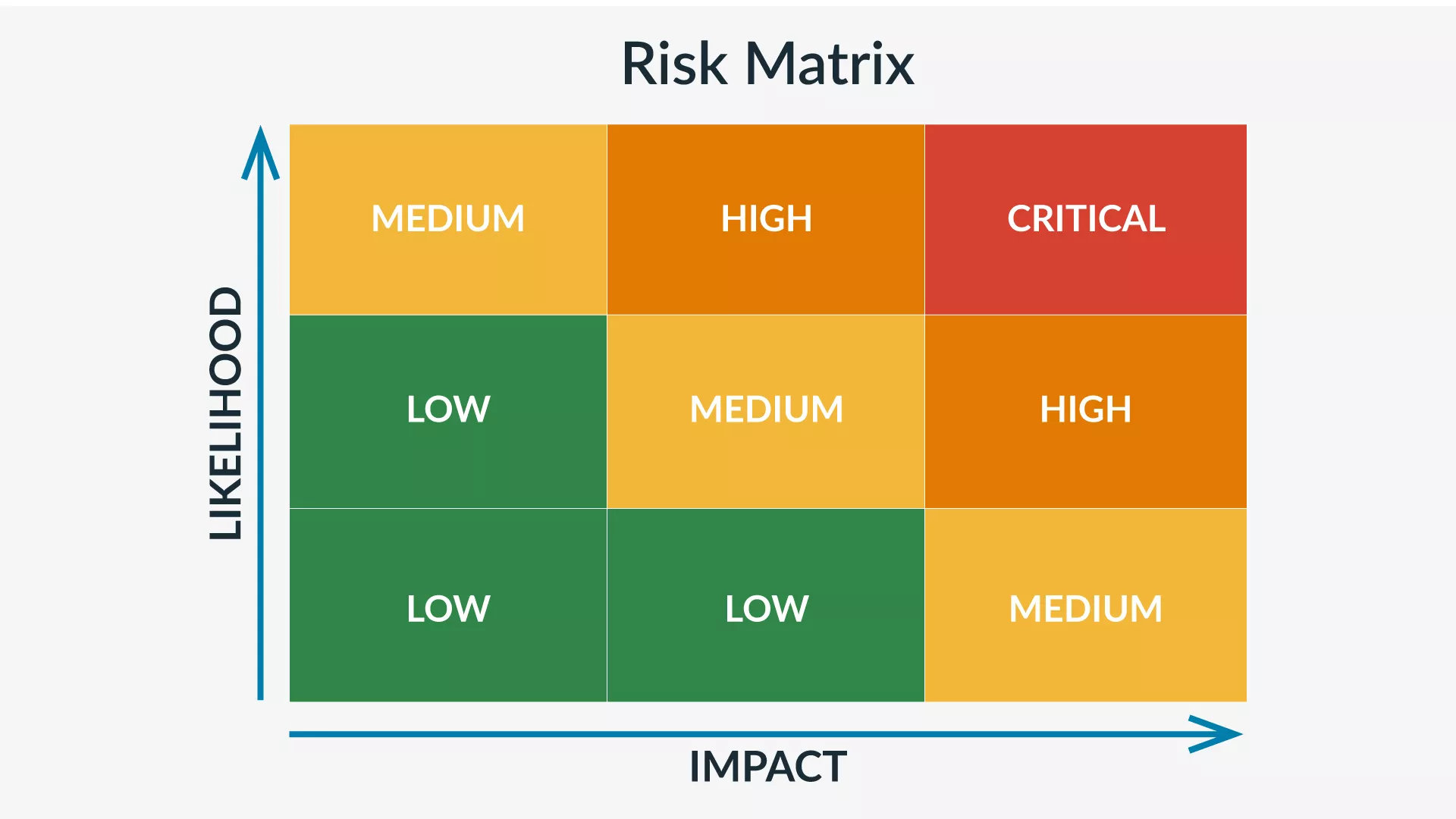
The matrix plots threats along two axes: likelihood, typically rated on a 5-point scale from “Improbable” to “Frequent,” and impact, often measured from “Negligible” to “Catastrophic.”
Take a winter storm, for example. For a business in the Northeast, the likelihood is high, but the impact is medium—assuming you’ve made smart preparations. In contrast, a terrorist attack is unlikely, but if it did occur, the impact would be massive.
The risk matrix is flexible, easy to use, and gives you a methodical way to assess potential risks, making it an essential tool for your security risk assessment.
Risk management frameworks
Use risk management frameworks to identify and manage global risks systematically. Proven options like COSO, ISO 31000, and NIST give you standardized tools to assess threats, stay in compliance, and boost security. An enterprise security risk management (ESRM) framework enables you to identify, evaluate, and mitigate security risks, ensuring efficient threat management while aligning with your objectives. Frameworks like the RIMS Risk Maturity Model® give you a clear process for evaluating how well your strategies work, so you can make improvements.
Threat intelligence
With critical events increasing in number and severity, you need a way to stay ahead of safety and operational risks. Threat or risk intelligence can enhance your security risk assessment tools by providing early warnings, contextual insights, and ongoing monitoring of emerging threats.
Companies like Walmart, JetBlue, and DHL use threat intelligence to track weather patterns, identify travel issues, learn from historical data, and validate threats in real time.
Threat assessment template
A security risk assessment template is one of the easiest ways to structure and document your findings. Our threat assessment template is a simple and straightforward tool to get started with—and it’s totally free.
Identify and describe relevant threats, decide which are most critical, and document the potential impacts on people, facilities, technology infrastructure, and more. The threat assessment template is your starting point for planning your preparedness and mitigation efforts.
How to Assess Security Risks in 5 Steps
If you’re ready to take control of your organization’s safety and security, here’s a simple 5-step process to follow.
1. Assemble your team
The first step is mobilizing a team to lead and run the project. Ideally, this team will consist of safety and security representatives from across the organization. At a minimum, you’ll want to include members from the executive, HR, and facilities management departments.
A diverse team of subject matter experts gives you the best chance of identifying all possible risks. For example, an operations manager or store supervisor can anticipate customer-related challenges. IT specialists will know which systems are most vulnerable to attacks. And finance pros will be able to point out potential fraud risks or identify financial trends that could impact resource allocation.
The risk assessment team will convene to identify and evaluate threats and develop prevention and mitigation plans for your business’s various threats. You may also want to engage external partners who play a role in response plans, like local law enforcement and mental health professionals.
2. Identify threats
Once your team is established, it’s time to get to work. Start by identifying all the potential hazards and risks that could impact your people and other critical assets.
It’s important to note the difference between hazards and risks. A hazard is anything that could potentially cause harm, while a risk is the chance that harm will occur and how severe it might be. For example, a hazard could be a wet floor in a busy lobby. The risk is that someone might slip and sustain an injury.
At this stage, it makes sense to categorize risks by type. This keeps things organized but also helps ensure you have all the bases covered. Major categories of risk include:
Internal threats
- Information technology vulnerabilities: Internet outages, systems downtime, corrupted data, IP theft
- Utility outage: Electrical power, water, sewage, air conditioning/heating disruptions
- Supply chain issues: Supplier failure, production delays
- Workplace accidents: Injuries, structural collapse, mechanical breakdown
- Hazardous materials: Gas leak, radiological accident, chemical spill
- Internal conflicts: Employee disputes, harassment
External threats
- Severe weather: Hurricanes, severe thunderstorms, blizzards, tropical storms
- Natural disasters: Earthquakes, wildfires, tsunamis, landslides, floods
- Biological: Disease outbreaks, pandemics, illnesses
- Transportation: Significant road closures, widespread flight delays, supply chain disruptions
- Communications: Cell coverage outages, power grid outages
- Suspicious activities or acts of violence: Active shooters, civil disturbances (riots), bomb threats, suspicious packages
Risks often appear in unexpected places, catching organizations by surprise. Case in point: Ryan Wallace, Associate Professor at Embry-Riddle Aeronautical University, discussed the growing concern of drone threats on The Employee Safety Podcast. He described how a single drone near Gatwick Airport disrupted over 1,000 flights, stranded 100,000 passengers for three days, and cost millions of dollars.
Beyond physical threats, make a point to recognize psychological risks, as they can have serious impacts on employees’ mental health and well-being.
Psychological threats
- Inadequate supervisor support
- Chronic burnout
- Excessive workload or unrealistic job demands
- Low engagement or lack of connection to the organization
- Poor communication or unclear expectations
- Limited opportunities for growth or recognition
- Workplace conflict or toxic work environments
A comprehensive risk assessment considers all of these risk types throughout the organization, from facilities and supply chain to HR and IT. For instance, the facilities team may focus on physical safety risks, the HR department on employee well-being, and the IT team on cybersecurity threats.
3. Assess threats
Not every risk will impact every company in the same way. When assessing threats, use your business’s specifics, including location, size, industry, business type, and historical data, to answer the question, “How will this risk impact my business ?”
Use a risk matrix in this step to assign a risk level based on factors specific to your business. For example:
- The risks for a small retail business with one storefront in a local shopping center will differ greatly from a global e-commerce platform with a network of warehouses and customers across multiple continents.
- A company in Florida is more likely to be impacted by hurricanes or flooding than a company in the Midwest.
- A business in California or Colorado may face greater risks from wildfires compared to one in a region with heavy rainfall.
When assessing threats, consider the impact on your people, locations, systems, and assets. This includes all environments where employees work, including remote, hybrid, and business travel situations.
Chad Bosques, Head of Physical Security at Chime, understands this well. To support remote employees, he used a tool called Workday, which tracks where employees are living. While the information is confidential, it’s invaluable during emergencies, like hurricanes in Florida or tornadoes in the Midwest. “We were able to know which Chimer was in the path,” Bosques explained on an episode of The Employee Safety Podcast. He then used a mass notification tool to reach out, ensuring employees’ safety and offering assistance.
4. Plan your responses
Once you’ve identified and prioritized potential threats, it’s time to plan your responses. This means developing and implementing controls to diminish the impacts of the threats.
The results of your risk assessment reports will directly inform the type of actions you’ll take. Imagine you discover that a major supplier is at risk of failing. In this case, you need to establish backup suppliers to ensure continuity. Or, if you operate in a region where severe winter storms are common, you’ll want to develop a disaster recovery plan and make provisions for your teams to work remotely if needed.
You can’t always prevent an emergency, but you can prepare for it. Thus, the goal here is risk mitigation: You want to minimize the likelihood and/or impact of the threats your business faces. Common controls include:
Train employees
The first and most basic control in enterprise risk management is employee threat assessment training. Make sure everyone in the organization understands what security incidents may occur, and how they may impact the employee’s role—and the business itself.
The most effective training involves active participation. So, test your emergency response plan with employees via drills or run-throughs. Use tabletop exercises to help them see the impact of a scenario and familiarize themselves with their roles in the event of an emergency.
Employee training also includes explaining the “why” behind protocols. As Bosques explained, people will often ask questions like “Why am I scanning my badge? Are you trying to track that I’m coming into the office?” He’s learned it can be really helpful to explain to employees that “It’s not my job to track you. My job is to make sure that you’re safe while you’re in the office.”
Enable cybersecurity software and tools
Cyberattacks occur with alarming frequency—data breaches exposed over 7 billion records in the first half of 2024 alone. Based on your security risk assessment, develop safeguards to protect your business systems and keep sensitive data safe.
For example, do you have strong firewalls and encryption tools set up? Do employees use multi-factor authentication to log into company platforms? Or, perhaps you need to expand your intrusion detection systems or security operations center.
Cybersecurity will only grow in importance, so set strong access controls now—your future self will thank you.
Create security policies
As every safety pro knows, the best time to prepare for an emergency is before it happens. Develop detailed, clear risk management plans to reduce the likelihood and impact of identified threats. For starters:
- Establish a policy for notifying employees about closures or delays during severe winter storms.
- Create a corporate travel policy to keep employees safe from potential threats while on the road.
- Clarify when to involve third parties, such as mental health services providers or law enforcement.
- Document emergency response plans with specific steps employees should follow in situations like fires, phishing attempts, or workplace injuries.
A security risk assessment is part of a broader risk management program, and your business processes are a major piece of that. The right set of policies lets you target critical vulnerabilities while staying adaptable to new challenges.
5. Evaluate your response
After you’ve identified, assessed, and responded to a risk, you need to evaluate your response. To start, reflect on the following questions:
- Did we properly assess the likelihood and impact of this threat?
- Was this threat avoidable?
- How quickly were we able to respond?
- Did we have the proper resources to address the threat?
- Did we have the appropriate controls in place?
- Was our communication effective?
And finally, the most important question: “What can we do better?”
Gather feedback from the entire organization to answer these questions thoroughly. You might think things went well, but employees might have a different idea. Were people confused or panicked during the incident? Did they know what to do and who to ask for help?
Bosques says engaging with employees and leadership is key. Ask them “Is this working? Is this something you think we should continue to do?” Real-life feedback, in combination with auditing your metrics and KPIs, is the best way to gauge your program’s success.
Repeat the process
New threats can emerge with the seasons, shifts in current events, economic changes, or advancements in technology. Even your workforce evolves over time. That’s why a security risk assessment isn’t a one-and-done task—it’s an ongoing cycle.
After you’ve evaluated the response and pinpointed areas for improvement, return to step one. Use the new insights and feedback to update your approach. Repeating the process ensures that you always have a current picture of the risk landscape and keeps your security program relevant.
Bosques says, “I regularly conduct assessments, typically every six months, to review the current state of the security program, identify any new technologies or challenges, and make necessary improvements.”
Progress, Not Perfection: Your New Mantra for Risk Management
There’s no such thing as a perfect response to a threat. Let that idea motivate you to keep improving rather than hold you back. With diligence and time, your security policies will mature, employees will become more confident with processes, and fewer issues will slip through the cracks. Ultimately, this means a safer environment for everyone and a business that’s stronger, more resilient, and better prepared to face whatever comes next.





