Hidden risks could pose a danger to your organization. Uncover them with a threat and vulnerability assessment.

Preparedness Starts With a Threat and Vulnerability Assessment

Proactive planning starts with recognizing that threats often build slowly—and that early action requires looking ahead. This forward-thinking approach is at the heart of any effective security strategy. As Lukas Quanstrom, CEO of Ontic, explained on an episode of The Employee Safety Podcast, “Protective intelligence is an investigative and analytical process used to proactively identify, assess, and mitigate threats.” That definition captures the structured mindset security teams need to spot and manage risks before they escalate.
Threat and vulnerability assessments offer a clear, repeatable way to surface those risks before they escalate. In this blog, we draw on insights from Lukas and established best practices to walk you through how to conduct one effectively so you can identify risks, evaluate impact, and take informed action before disruption strikes.
Identify your business’ most critical threats with this fill-in-the-blank template.
What Is a Threat and Vulnerability Assessment?
A threat and vulnerability assessment, also known as a threat and vulnerability risk assessment or TVRA, is a methodology of vulnerability management to protect your organization from any possible disruptions. It’s a critical component of all-hazards preparedness and incident response.
By cross-referencing a deep understanding of your business assets and processes with a comprehensive external threat outlook, any organization can improve its business resilience and benefit from the often-unseen efforts of safety and security teams. Let’s look at each of its constituent parts:
Assets Anything your business owns or uses that contributes value to operations. Examples:
| Vulnerabilities Security weaknesses in assets that expose them to threats. Examples:
| Threats External or internal events with the potential to cause harm. Examples:
| Risk The likelihood and impact of a threat exploiting a vulnerability. Examples:
|
How to Perform a Threat Vulnerability Assessment
Analyzing your business and its operational environment is key to a successful threat vulnerability assessment. Lukas Quanstrom explained, “By adapting a mindset shift to a proactive, always-on security approach, you can continually collect and connect pre-incident physical threat indicators… to prevent bad things from happening.”
Taking that proactive approach, you can follow the six steps below to help you identify, assess, manage, and mitigate your potential vulnerabilities.
1. Catalog threats
Businesses don’t operate in a vacuum. Both internal and external threats can spell varying degrees of disaster for your critical assets and operations. Before you focus on threat mitigation, you must first know and understand those threats in their entirety.
The best way to do that is with a threat catalog. Identifying and listing every known threat in your area will open new perspectives on your organization’s preparedness.
Threats can be anything with potential adverse effects. Don’t worry about how these potential risks would impact your business—we’ll get to that later. Remember that threats can be internal (from within the company) or external (from outside the company).
First, gather business leaders and stakeholders to brainstorm a written list of every potential threat in your physical area, within your company, and those not tied to physical locations, such as common computer viruses or other cybersecurity threats.
From there, the group should answer the following questions for each potential threat:
- Where does it originate?
- How common is it?
- Has it affected the organization before?
Lukas emphasized the value of spotting warning signs early, whether a pattern of concerning behavior or an anomaly in access logs. Organizations can prevent escalation and act before disruption by treating these signals as meaningful, even if they don’t yet point to a confirmed threat.

Physical security
Poor access control to your workplace encapsulates many security gaps and risks. Active shooters, property theft, converged security threats, and even nuisances that disrupt the work environment all fall into this category.
Information technology
A popular target among threat actors these days, anything that stems from your computer systems belongs in the IT risk category. This includes the increasingly prevalent threat of cyberattacks like hackers, ransomware, and sensitive data breaches, but also encompasses human-based threats like phishing attacks or catastrophic user errors.
During his interview, Lukas noted how many cybersecurity risks have become harder to track as employees shifted away from centralized offices. “The threats have been pushed away from the office… and dispersed into geography,” he explained, pointing out that remote work has stretched security teams across “a wide patch of less secure turf.” With business-critical tasks now being handled from homes and personal devices, IT vulnerabilities and cybersecurity risks are no longer confined to a controlled corporate environment.
Natural
From hurricanes to earthquakes to global pandemics, the natural world has a varied arsenal of threats to your business. Of course, this category is vast. Depending on the threats in your area, you might want to break it up into sub-categories such as natural disasters and hazardous weather.
Socio-political
Civil unrest, protests, laws, curfews, and other factors can profoundly impact a company’s ability to continue operations. As a part of the larger society, your business can’t be completely insulated from those forces.
2. Analyze assets
To understand your business as a complex system, you must first understand its constituent parts. The best way to do so is to create an “asset record.” This record will be an authoritative list of all assets and their key attributes.
Collaborate with department leaders to ensure you don’t miss anything. Those leaders are usually well-versed in how assets under their purview work and fit into the larger business apparatus, so including them from the start will save time and effort. It’s a good idea to organize attributes by categories, such as by departmental owner and location.
For each item on this list, consider how it fits into your larger business ecosystem. The following questions can help guide your efforts:
- Who is responsible for the asset?
- Who works with it?
- What are its inputs?
- What does it output?
- What other assets/systems rely on this?
- Has it failed or become compromised before?
- If so, how? And how did you recover it?
- Are we aware of any alternative?
As Lukas pointed out, subtle signs, like unusual movement between facilities or deviations in access control, can offer early insight into potential vulnerabilities. These patterns don’t always register as obvious threats, but when viewed in context, they help security teams connect the dots. A complete asset record gives you a more transparent lens for spotting this type of activity, revealing risks that might otherwise go unnoticed.
3. Determine vulnerability
At this stage, your organization should have a detailed list of assets and a working catalog of relevant threats. The next step is to examine the relationship between the two and identify where your assets are most exposed.
Start by asking: Which assets are most likely to be affected by which threats? Not all threats impact all assets equally. For example, a ransomware attack might affect your customer service systems but have little effect on your HVAC infrastructure. Similarly, a power outage could disrupt in-branch operations but leave your cloud-hosted systems untouched.
As you pair assets with threats that could realistically affect them, you can begin assigning a vulnerability rating to each pairing. Depending on the level of precision you need, this can be done using a simple scale—low, medium, or high—or a more granular numerical system.
- Low vulnerability: The asset is unlikely to be affected by the threat, or existing controls provide strong protection.
- Medium vulnerability: There is some exposure, and existing controls may not be reliable or consistently applied.
- High vulnerability: The asset is exposed and lacks sufficient protections. A successful threat event would likely lead to significant disruption or loss.
This is a time-consuming process, but it’s the heart of vulnerability analysis. By comparing your assets with each identified threat, you’ll paint a detailed landscape view of your organization’s vulnerabilities.
4. Predict impact
After analyzing your assets’ vulnerabilities, the next step is to consider the consequences. Predicting impact means asking what would happen if a specific threat affects a vulnerable asset. This step is less about likelihood and more about severity.
Focus on what the disruption would mean for operations, finances, safety, or reputation. Could it halt a critical process? Would it affect customer trust? Would it cause compliance violations or physical harm? The more essential the asset and the more far-reaching the outcome, the greater the impact.
As Lukas explained, once you identify a potential threat, “the next step is to research the threat and apply data… so that you can learn as much as possible.” That knowledge informs how you assess severity and determine the threat’s impact on your organization.
You can categorize impact using the same tiered scale applied earlier:
- Low impact: Minimal disruption, no long-term consequences.
- Medium impact: Noticeable disruption, may require manual workarounds or limited downtime.
- High impact: Major disruption to operations, legal implications, safety risks, or financial loss.
This classification helps guide the next phase—synthesizing risk—by giving context to how damaging each threat-asset pairing could be if left unaddressed.
5. Synthesize risk level
Once you’ve gathered your vulnerabilities and impacts, it’s time to plot them on a threat matrix, much like you do with a business threat assessment. A threat matrix is a grid on which you can visualize the likelihood and severity of any given vulnerability. The X-axis represents likelihood, while the Y-axis represents severity.
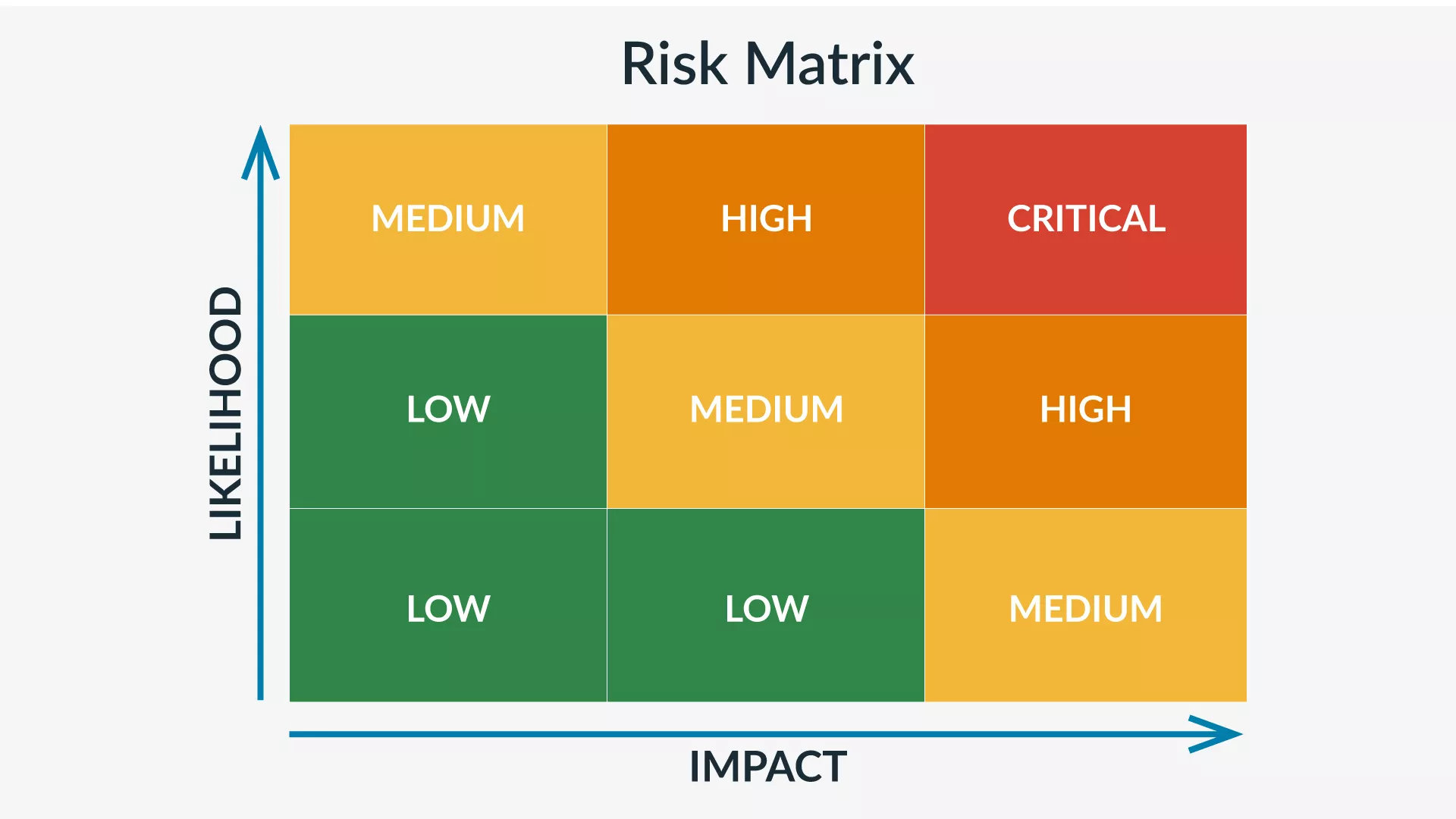
You’re then left with a visual representation of the risk level of each asset’s vulnerability. Vulnerabilities with a high likelihood and high impact are high risk, those with low likelihood and impact are low risk, and some vulnerabilities fall in the middle.
6. Devise solutions
Once you’ve determined risk levels, you can focus on remediation and response. It may be more practical to accept risks with very low impact and likelihood, particularly when the effort to mitigate outweighs the benefit. For example, you might choose to use a third-party web application that lacks specific advanced controls but only handles internal scheduling and does not store sensitive data. The risk is low enough that you can accept it.
High-likelihood, high-impact risks should be addressed as a priority. For example, if your school is located in a hurricane-prone region and lacks a reinforced shelter or a reliable communication system, the likelihood of severe weather combined with the potential for injury and operational disruption makes this a top priority for mitigation. Installing reinforced safe zones and automating weather alerts and lockdown protocols would be critical next steps.
The countermeasures to any of these vulnerabilities are as varied as the risks themselves, so work with the team that helped with the asset analysis and threat catalog to determine the most effective responses. With the risk levels in mind, your brain trust will have a much easier time preempting and intercepting any business disruptions and undertaking successful risk management.
Risk mitigation requires continuous improvements and monitoring of your attack surface. Lukas emphasizes the importance of continuously monitoring threats by tracking public records, staying aware of situational changes, and using real-time alerts to catch risk shifts. Risk levels can change quickly as new information emerges, so it’s essential to revisit your assessments regularly and adjust your countermeasures as needed. A solution that worked yesterday may no longer be effective tomorrow.
Tools and Methodologies That Support Assessments
Leaning on established frameworks and proven tools helps make your threat and vulnerability assessment process reliable and repeatable. Methodologies bring structure to your process, and technology makes it easier to carry it out consistently and catch risks before they escalate.
| Methodologies | Tools and technology |
| Methodologies give your team a shared approach to identifying and evaluating threats. They also help ensure your assessment can scale across departments and hold up to outside scrutiny. | Technology plays a key role in executing and maintaining your assessment process. It can help surface security vulnerabilities faster, reduce manual effort, and improve coordination across teams. |
|
|
Examples of Types of Vulnerability Assessments
All types of vulnerability assessments can follow the same six steps, no matter how different they are. Below, we’ve laid out a few threat assessment examples and how leaders can apply them in IT systems, for physical security, or in different physical environments.
Example #1: IT vulnerability assessment in banking systems
A regional bank with 10 branches conducted an IT vulnerability assessment to evaluate cyber threats across its distributed infrastructure. The team followed the six-step process outlined:
1. Catalog threats
The bank identified a mix of internal and external threats. These included phishing, malware, ransomware, firewall misconfigurations, outdated network security, and weak access controls. Additional risks included staff errors, decentralized patch management, and inconsistent surveillance logging across locations and endpoints.
2. Analyze assets
Key digital assets were identified, including branch-level workstations, core banking servers, network firewalls, and email systems. Several branches were running legacy operating systems, and some remote login tools lacked multi-factor authentication. Roles and responsibilities for managing these assets varied across branches.
3. Determine vulnerabilities
The team cross-referenced threats and assets to identify areas of most significant exposure. Systems running outdated software were rated highly vulnerable due to known exploits. Branch workstations with unrestricted internet access were also marked high. Email systems had moderate exposure to phishing, with inconsistent user training and filtering in place.
4. Predict impact
The team evaluated the consequences of a successful attack or failure. A ransomware incident on a branch server could disrupt customer transactions and access to account data—classified as high potential impact. Email compromise through phishing was rated medium impact, with potential for reputational harm and limited service outages.
5. Synthesize risk level
Using a risk matrix, the team mapped vulnerabilities by likelihood and potential impact. Phishing and unpatched systems emerged as high-risk issues due to their frequency and potential to disrupt business-critical operations. Firewall misconfigurations and decentralized asset oversight were ranked medium risk.
6. Devise solutions
The bank developed a remediation plan that included centralized patch management, firewall policy standardization, and rollout of multi-factor authentication. Mandatory security awareness training was introduced for all employees, and a unified threat monitoring system was deployed across all branches.
Example #2: Physical security assessment in facility access controls
The regional bank expanded its vulnerability assessment to focus on physical security threats involving instrumental violence. These include acts such as robbery, forced intrusion, or sabotage designed to achieve a specific objective.
1. Catalog threats
The bank identified targeted threats, including armed robbery, forced entry during off-hours, unauthorized access to vaults or teller stations, and impersonation tactics used to bypass front desk protocols. Instrumental violence was considered a primary concern, especially in branches located near high-crime corridors or operating with minimal on-site security.
2. Analyze assets
The assessment reviewed all physical security controls related to high-value areas: entry points, secure transaction counters, vaults, employee-only corridors, surveillance systems, and panic alarm setups. Inconsistent use of badge systems and limited visibility in exterior zones created blind spots that could be exploited during a planned attack.
3. Determine vulnerabilities
Branches with limited physical barriers, outdated locking mechanisms, or unmonitored access points were rated high vulnerability. One branch had no secure employee-only entrance, and another had rear exits without functioning alarms. Locations without visible surveillance or staff coverage were also flagged.
4. Predict impact
A successful breach or robbery attempt could result in staff injury, cash loss, reputational damage, or a temporary shutdown. These scenarios were classified as high impact, given their potential to disrupt both operations and customer trust.
5. Synthesize risk level
Using a risk matrix, the team found that branches with high foot traffic, limited staff, and weak perimeter controls faced the most significant threat. Locations with outdated surveillance and no remote monitoring were also prioritized.
6. Devise solutions
The bank responded by upgrading surveillance systems to include real-time monitoring, reinforcing staff-only barriers, and installing duress alarms in teller zones. It also standardized access control across branches, conducted instrumental violence response drills, and trained staff to quickly recognize and escalate suspicious behavior.
Example #3: Assessing physical security in a manufacturing plant
A small manufacturing facility with 40 employees conducted a physical security assessment to address safety and access risks tied to its operations and layout.
1. Catalog threats
The assessment team identified key threats, including unauthorized access to restricted areas, theft of tools or materials, tampering with machinery, and workplace violence. The open layout and lack of full-time security staff increased the likelihood of unnoticed intrusions or internal misuse of equipment.
2. Analyze assets
Assets reviewed included production machinery, tool storage areas, employee entry points, perimeter fencing, internal surveillance systems, and badge access controls. Some entry points lacked surveillance coverage, and key equipment zones had no physical barriers preventing unauthorized entry.
3. Determine vulnerabilities
The team flagged several high-risk areas: unlocked doors near loading docks, limited visibility in blind corners of the shop floor, and shared key access to sensitive areas like control panels. The facility had no real-time monitoring in place, and visitor sign-in procedures were inconsistent.
4. Predict impact
A breach of secure zones could result in equipment damage, production delays, or serious injury to unauthorized personnel. Theft or sabotage of high-value tools could disrupt operations and lead to financial losses. These events were classified as high-impact due to the direct threat to safety and business continuity.
5. Synthesize risk level
A risk matrix helped the team prioritize issues based on likelihood and severity. High-priority risks included unsecured entry points, lack of internal surveillance, and untracked visitor access to sensitive production areas.
6. Devise solutions
The plant installed badge-controlled access for all secure areas, expanded surveillance coverage to blind spots, and implemented a mandatory visitor check-in process with escorts. Storage for high-value tools was reinforced and locked, and employees were trained in recognizing and reporting suspicious activity.
Example #4: Enhancing natural disaster preparedness in schools
A mid-sized school district conducted a physical vulnerability assessment to better understand how prepared its campuses were for natural disasters such as hurricanes, floods, and severe storms.
1. Catalog threats
The district identified primary threats based on regional weather patterns and historical data. These included high winds, flash flooding, power outages, and structural damage from hurricanes or severe storms. They also considered secondary risks, like blocked evacuation routes and disrupted communication systems.
2. Analyze assets
Key assets included building infrastructure, backup power systems, evacuation maps, emergency supplies, and communication tools. Many schools lacked reinforced storm shelters or had outdated intercom systems that wouldn’t function during power failures.
3. Determine vulnerabilities
Schools located in low-lying areas without adequate drainage were marked high risk for flooding. Campuses with aging roofs, single-entry bottlenecks, or no formal reunification protocols were also flagged. Several facilities had no staff trained in disaster response.
4. Predict impact
The district concluded that without better safeguards, a major storm could leave students and staff stranded, lead to structural failures, or result in injuries and prolonged closures. The loss of instructional time and community confidence was classified as a severe operational and reputational impact.
5. Synthesize risk level
Using a risk matrix, the district prioritized schools where poor infrastructure, high-threat exposure, and low preparedness intersected. Special attention was given to campuses serving younger students and those with complex transportation needs.
6. Devise solutions
The district reinforced roofs and entryways at high-risk campuses, installed backup generators, updated emergency communication tools, and stocked each school with disaster kits. Staff underwent annual training on shelter-in-place procedures, evacuation coordination, and parent communication strategies.
These examples, from banks and manufacturing plants to school districts, show how a structured threat and vulnerability assessment process can be applied across vastly different environments. While the specific threats, assets, and vulnerabilities vary, the same six-step framework helps each organization evaluate risks in context, prioritize what matters most, and take meaningful action.
Putting Structure Into Practice
A well-structured threat and vulnerability assessment is one of the most practical ways to improve organizational resilience. As Lukas Quanstrom noted, this approach gives “teams a repeatable, disciplined way to assess threats and reduce risk before disruption occurs.”
Whether you’re working to protect digital systems, industrial equipment, or people on a campus, the six-step framework provides a consistent way to uncover risk, prioritize response, and justify proactive investment. The examples in this guide show how the same process can apply across very different environments, giving safety and security teams the structure they need to take action.
By following best practices and using the right tools, organizations can move beyond reactive thinking and build a culture of preparedness. When you use our Threat Assessment Template, you won’t feel like starting from scratch with this high-stakes task.


![How To Make Risk Mitigation Work [+Template]](https://www.alertmedia.com/wp-content/uploads/2023/01/Risk-Mitigation-Steps-Blog-V1.jpg)

